Why more tools are needed in Cyber Security and why I conceived Dracoeye
There’s loads of great tools out there for the Cyber Community to use in identifying bad actors, but there’s a gap for collecting the output of these services in one place and that is the reason why you need Dracoeye in your toolset.

This is a guest post by Rich Benfield, Director of Technology at Th4ts3cur1ty.company and Product Owner for the Dracoeye project.
What is Dracoeye?
We’re blessed in our industry to have a thriving community that brings us tools we use daily, almost exclusively free to help us do our jobs. You don’t need to look far to find many services that help identify IOCs (Indicators Of Compromise) such as Threat Fox, Virus Total or Alien Vault. Here comes the first hurdle; while these tools are excellent, I identified an opportunity to streamline threat analyses by bringing the summaries of these tools to one place, saving valuable time during, quite often, high-pressure and stressful situations.
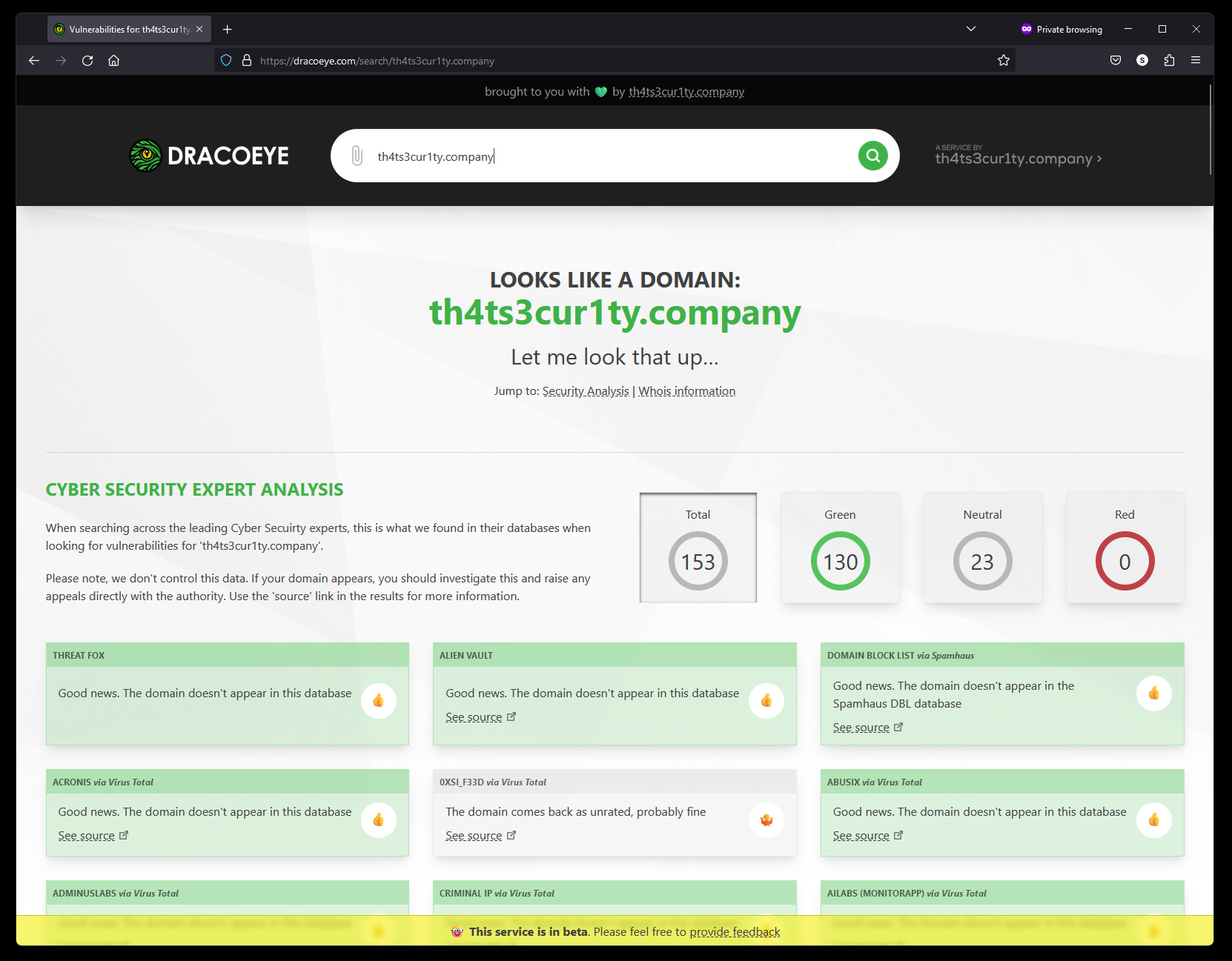
Moreover, different checks of compromise require different services. When identifying bad actors for email, we may turn to Blacklist Checker or Spamhaus. For checking file hashes we might turn to MHR (Malware Hash Registry) by Team Cymru or Virus Total. For domain or IP checks we might turn to Alien Vault and Virus Total, you get the idea. There’s an opportunity to bring all of our community tools together to get that quick overview, then jump into those services to gather the details. This is why I conceived the idea of Dracoeye and why my team developed it.
What next for Dracoeye?
As part of root cause analysis, we often want to go beyond finding IOCs, we also want to understand how a compromise happened in the first place. From here, employees in companies can be educated to better understand security hygiene and also ascertain whether a system compromise was the consequence of a third party being compromised.
Cyber Security goes beyond identifying IOCs
Again, our community is blessed with services like Have I Been Pwned to discover this. As with identifying IOCs, this is another check and maybe a resource that isn’t part of your toolset (yet). By expanding the reach of Dracoeye in the future to include these kinds of check, you can gather that holistic view of not only what the compromise consists of, but how it happened - all in one place.
We need your feedback
As an organisation, we’ve already stated, “this is just the beginning”. My team is working hard to implement the suggestions and tools that make your life easier, and the feedback has been brilliant. We’ve enjoyed working together on this project and I encourage you to check out Dracoeye.com for yourself and feedback to us on what is important to you in the course of your work duties.

